SERVICES
POLICIES
-
IMPLEMENTATION OF INFORMATION SECURITY MANAGEMENT SYSTEMS
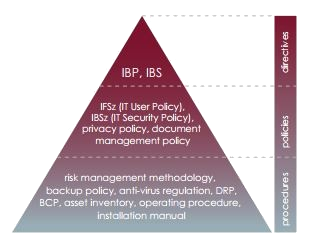
Electronically stored and processed information are the key assets of companies. Their protection therefore is a fundamental objective for every organization.Information Security Management System (ISMS), a system based on best practices organizes information protection activities ranging from the top management’s willingness to take risks to the development of policies for the whole organization as well as the management of information technology tools into a coherent framework.Organizations need to create the following documents and policies for implementing an ISMS:
- Document management and archive policy,
- Acceptable use policy,
- Confidentiality policy,
- Risk management policy,
- Information security policies,
- information security strategy,
- Business continuity plans,
- Information asset inventory,
- ISMS access control policy.
 Our services include the following:
Our services include the following:- developing ISMS documents;
- assisting organizations in creating policies;
- helping organizations implement security controls;
- providing training.
Our methodology conforms to the requirements of the ISO 27001 standard. Information security management systems developed by kancellar.hu will help organizations achieve compliance with the ISO 27001 standard. -
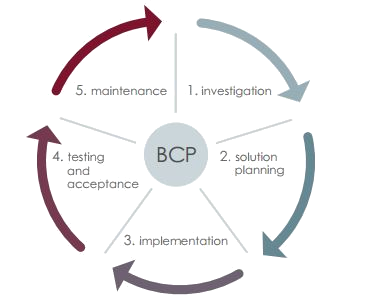
BUSINESS CONTINUITY PLAN
The objective of business continuity planning is to systematically assess the continuity requirements of the organization’s business processes, the consequences of interruptions, and to take preventive actions against unacceptable downtime (i.e. critical events).The result of business continuity planning is a Business Continuity Plan (BCP) that helps organizations effectively recover critical business processes in the event of a major disruption.Business continuity plans should be regularly reviewed (e.g. annually, or whenever a new system is implemented etc.). The Business Continuity Management System, by defining the ways of handling changes in requirements and external conditions, keeps the plan a living document.Our services include the following:
- identifying critical business processes;
- identifying operational and financial impacts, defining security gaps for each process and the extent of damage arising from interruptions;
- proposing measures that ensure business continuity;
- proposing a framework of business continuity management (BCM);
- developing business continuity plans (BCP);
- providing help during the preparation phase;
- providing help with testing and training business continuity plans.
-
DISASTER RECOVERY PLAN
IT systems do not only provide a solid basis for businesses but their elements are closely interconnected and interdependent.In such a situation, it is critical to determine the impact of a disruption of the IT systems on other systems, to identify the cause of the disruption and, most importantly, to find out how long the recovery process will take.The objective of disaster recovery planning is to set up security controls to prevent disruptive events and interruptions leading to unacceptable consequences (i.e. critical events). The Disaster Recovery Plan is a document that provides detailed advice on how to deal with disasters, steps to take to prevent such a disaster and tasks to perform after such a disaster. It defines roles and responsibilities in the recovery process and contains information that is relevant for a successful recovery.Our services include the following:
- assessing business critical applications and IT resources supporting such applications;
- identifying threats and their impacts on IT systems by using FMEA method (Failure Mode and Effect Analysis);
- performing a risk analysis based on the impact of potential threats on IT systems, identifying events that can be dealt with in business operations;
- recommending measures to manage unacceptable risks and, if required, creating a detailed disaster recovery plan.
The result of disaster recovery planning is the development of a Disaster Recovery Plan defining- emergencies,
- conditions for an emergency,
- general business management rules to follow in an emergency,
- business processes that are affected (critical business processes),
- disaster events and their causes,
- general preventive and defensive measures,
- detailed action plans to follow during recovery.
-
RISK MANAGEMENT
Information security is a ’weakest link’ problem. The costs of information security controls should be proportional to the value of protected information. An adequately designed and operated risk management system ensures that information security systems are risk-based and proportional. We assess the value of IT assets and reveal vulnerabilities to define controls that are proportional to the likelihood of an adverse event and the severity of the consequences of such events (harm).Risk management is an ongoing process where the measure of success is not always to find the optimal solution but to
- provide an overall and objective analysis to ensure continuous quality performance;
- enable organizations to evaluate recommended controls based on a cost-benefit analysis;
- provide feedback to evaluate the effectiveness and efficiency of decisions;
- use internal benchmarking to monitor exposure to risks.
For us, risk management methodology is similar to weather forecast: we can never be certain about the completeness of input data nor can we trust that the method used will give us a realistic picture. However, the model can be improved by continuously evaluating results. Similarly, risk management methodology can be improved constantly by regularly evaluating and analysing organizational knowledge.Our services include the following:- defining the scope of the assessment;
- identifying assets and vulnerabilities;
- defining and analysing risks:rint:
- evaluating existing security controls and the effectiveness of countermeasures; carrying out vulnerability assessment;
- defining potential losses;
- defining frequency of events;
- recommendations for managing risks.
We will deliver a risk management methodology that will be aligned with the needs of your organization, a risk analysis report and a list of recommended countermeasures. -
INFORMATION SECURITY INCIDENT MANAGEMENT POLICY
Over 300 software vulnerabilities and more than 500 new viruses are detected each month. Due to ongoing attacks intrusion prevention systems flood users with alerts. By using the right technological tools out of the several million alerts and log entries you can select those 5-20 important daily incidents that should be dealt with.Our service provides a framework for managing incidents that are detected by any of your organization’s information security tools. All security incidents (including privacy incidents) should be addressed to in progress, following the organization’s incident response lifecycle. It is necessary to know what the criteria are for security incidents (and which security incidents are to be dealt with as privacy incidents) and how to prioritise. Security incidents include new vulnerabilities on the Internet, new patch files provided by software vendors, virus epidemics, vulnerabilities revealed in our own network, and external threats, just to name the most common examples. When and what instructions should be followed, which organizational units should be involved – the HR, the legal or the marketing department? These questions need to be answered before the first incident occurs.The organization’s incident management policy sets forth the rules for detecting and reporting security incidents as well as the responses and processes afterwards, and defines the roles, responsibilities and, in particular, the rights of the participants.Our services include the following:
- Making an assessment of the organization’s security environment;
- defining the method of identifying and reporting incidents;
- recommending the organizational background for implementing countermeasures;
- defining the method of handling incidents;
- defining incident response lifecycle model;
- giving users training in how to detect and report incidents.
Our incident management service will provide you with an incident management policy, which forms step 3 of the ISMS Framework.
AUDIT SERVICES
-
INFORMATION SECURITY AUDIT BASED ON ISO 27001
The ISO 27000 family of standards is a generally accepted and extensively used standard for information security management. It has a complex, systematic and practical approach to information security.The objective of the audit is to give answers to the following questions:
- How safe is the organization?
- What are good practices and what changes are required immediately?
- How cost-effective is the operation?
- What future measures should be implemented to improve the organization’s information security and how much time/money/energy do they require?
Our services include the following:- assessing the overall information security environment of the organization, focusing on the following areas:
- human resource and administrative security,
- physical and environmental security,
- communications and operations security,
- access control,
- security of information system’s development and maintenance,
- structure of information security management system, implementation of controls;
- making a detailed proposal to mitigate risks considered critical;
- presenting our findings and recommendations to the top management in a workshop.
Our audit service will provide:- a detailed audit report documenting the audit process and our findings;
- a recommended short, medium and long-term action plan including estimated costs and resources;
- a brief executive summary of our findings.
-
IT GOVERNANCE, COBIT AUDIT
CobiT, Control Objectives for IT and Related Technology, is a set of best practices for information security governance. The fact that the National Bank of Hungary involved CobiT into MNB recommendations and audits greatly encouraged its spread and increased its popularity. The advantage of using CobiT is that it has a complex approach to all areas of IT governance, deriving IT objectives from business objectives and assigning controls to be implemented to objectives. The CobiT maturity model can be used to measure the maturity and capabilities of organizations’ IT processes.In our experience IT security systems cannot be operated efficiently without well-established IT security governance. Ideally, the two areas evolve ‘hand in hand’, results achieved in IT governance have a positive effect on security and also, security requirements encourage the development of IT governance.Our services include the following:
- assessing the organization’s IT processes by using CobiT control areas and objectives;
- assessing the organization’s IT processes (using the CobiT maturity levels);
- presenting our findings to the management.
Based on the structure and philosophy of the standard, the audit will provide you with a comprehensive picture of your IT infrastructure, assessing IT processes and helping you understand where your organization stands in the maturity model.As a result of the audit, we will deliver a report and identify the maturity level of the various CobiT areas of your organization.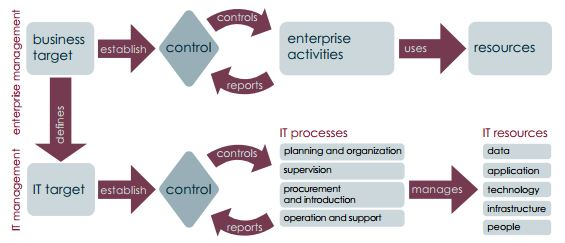
-
LEGAL AUDIT OF IT SECURITY POLICIES
One of the key areas of information security is compliance with laws and regulations. Legal compliance requires special knowledge and dedicated resources as this problem is usually too technical for the legal and internal audit department and too legal for the IT department. The fact that the law is always behind technology only makes the situation worse and therefore many organizations are faced with the problem of interpreting legal requirements.Our service is based on our experience gained in a large number of governance projects where we examined a whole range of aspects of legal compliance and considered information security issues from a legal standpoint.In regard to the fact that legal regulations predominantly require a documented and regulated approach to business operations, this service is recommended to organizations that already have an information security policy in place.Our services include the following
- collecting laws and regulations that affect the operation of your organization;
- identifying requirements for processing information within your organization;
- checking your organization’s security controls against requirements;
- making a proposal for implementing controls.
At the end of the audit, we will deliver a report with our findings. -
ETHICAL HACKING
Ethical hacking is a real-life security test revealing system security deficiencies by imitating an attack.Before planning the test, we determine the amount of information made available to potential hackers (in this case the ethical hacker) as well as the duration and costs of the test as our objective is not to prove that a system is unbreakable but that it can withstand attacks carried out by using a fixed amount of resources.Accordingly, we offer three types of ethical hacking tests:
- Black box testing simulates a typical hacking attack, requiring only minimal information about the system (e.g. IP address). The objective of the test is to evade the system’s security controls.
- Gray box testing means that we are given user login rights to analyse the system. This test is recommended if you want to know how valid and authorized users can threaten your systems.
- White box testing means that all information is available for testers about the system or application (source codes, administrator rights to the operating system, configurational settings of the systems, password files, firewall rules, IT security policies, manuals etc.). The investigation will give us a comprehensive picture of the system.
The advantages of kancellar.hu’s solutionKancellar.hu’s audit and penetration testing methodology is based on many years of professional experience. This methodology is a refinement of the widely accessible recommendations and standard initiatives (OWASP, OSSTMM). With the help of this methodology our specialists produce high quality project deliverables for our clients.Based on our experience of over 300 accomplished tests, having sufficient knowledge of the operation of the specific application system and its business infrastructure is essential to identify high level risks. In practice it means that testers must have specialized knowledge about the particular system, including:- its specific services,
- its specific functions,
- types of attacks that can be carried out using its functions, and
- widely used technologies and infrastructure relevant to the system.
Based on our penetration testing experience we believe that using automated penetration testing tools without highly qualified testers will not produce the desired result.Tests that are carried out within a few days and are based exclusively on the results of automated tools will generally identify only few of the real vulnerabilities, and the false alarm rate is usually high. Therefore, these results can rarely be used to enhance security in practice. In our audit projects we provide our clients with a team of qualified specialists whose experience is a guarantee for thorough testing.We would like to call your attention to the fact that in case of penetration tests and vulnerability assessments the depth of an analysis will usually be directly proportional to the amount of time devoted for the test—test results will indicate what vulnerabilities can be detected or what access rights can be accessed by using specific resources. For this reason, the depth of the analysis should always be defined according to the (estimated) value of sensitive information or processes and we will take this information into account when defining deadlines in our proposals.Our services include the following:- selecting testing methods and information to be shared beforehand (together with clients);
- gathering information and planning penetration tests;
- performing tests. Testing covers predetermined IT components. Risky testing phases are agreed with clients beforehand;
- documenting our findings and describing revealed vulnerabilities, defining possible preventive countermeasures and proposing solutions.
-
WIRELESS AUDIT
Growing use of wireless technologies substantially increases their user friendliness. Incorrect configuration, however, poses a previously unknown threat to organizations. Our service covers the security audit of your wireless communication systems.The first phase of the audit is an assessment of active and passive network components, when the running firmware’s version numbers are collected, and authentication and encryption processes are analysed. The configuration of work stations and servers will also be examined. Data that are processed through the inspected infrastructure will be identified to ensure compliance with the Data Protection Act.Afterwards vulnerability tests will be conducted to assess the security of your IT systems in terms of confidentiality, integrity and availability. The software we use for vulnerability tests are the same as potential hackers would use: sniffer and portscan software to gather data, vulnerability databases, DoS attack software, exploit databases. Systems will first be tested for confidentiality, mainly for gathering further data (sniffer, portscan). Afterwards we will use tools to test availability and integrity.Our services include:
- making an assessment to gain information about the topology of your wireless network solutions;
- carrying out vulnerability tests to identify existing vulnerabilities;
- making proposals for the elimination of vulnerabilities;
- presenting our findings.
The result of the audit is a report summarizing the methodology used, revealed vulnerabilities and recommended countermeasures. -
TESTING VIRTUAL SOLUTIONS
Virtualization is the creation of virtual tools/resources out of physical tools/resources. Because of its advantages (cost effectiveness, simpler administration, flexible ways to meet business needs) virtualization is more and more extensively used even in critical information technology systems.In addition to its operational benefits virtualization also poses new security challenges for organizations:
- the breakdown of a server may lead to the loss of several services;
- if a virtual server is compromised, it increases the threat level of several systems,
- roles become less clear-cut (network administrator, operating system administrator, SAN administrator etc).
Security issues may arise in the following connections:- physical data network, internet – virtual host
- virtual host – hypervisor/host operating system
- virtual host – virtual host
- physical data network – service console
- physical data network – management centre
- connections between virtualized data network and virtual hosts.
We use manufacturers’ security recommendations and documents, configuration analysis software tools to gather relevant configuration components and analyse vulnerabilities in the specific IT environment in order to identify irrelevant weaknesses.Our services include:
Exploring vulnerabilities of the listed connections by performing configuration analysis for the virtualized systems.At the end of the testing phase, we will deliver a report documenting our findings as well as our recommendations for mitigating threats. -
PREPARATION FOR THE COMPLIANCE WITH THE GENERAL DATA PROTECTION REGULATION (GDPR)
From 25 May 2018 the new EU General Data Protection Regulation (Regulation 2016/679/EU – GDPR), which fundamentally changed the previously effective data protection rules in Hungary (and in all EU countries), applies to data controllers (who individually or collectively determine the purposes for which and the means by which personal data is processed) and data processors.Although in theory the GDPR can be regarded as the revision of the previously effective directive, in practice it introduced several new requirements which pose a considerable challenge for data controllers and data processors (e.g. data protection by design and by default, principle of transparency, accountability principle, right to be forgotten).A significant novelty of the regulation is that data controllers are required to implement appropriate administrative as well as technical measures in order to demonstrate compliance. For this reason, we believe that although this task primarily requires legal knowledge, it cannot be carried out without involving IT specialists.Our services include the following:
- mapping personal data processed by data controllers,
- making an assessment of compliance of data controller’s current organizational culture and its activities with the GDPR,
- identifying actions and their priority to help organizations demonstrate compliance with the Regulation,
- providing organizations help in performing identified actions, such as:
- creating data controller’s privacy and data security policy,
- creating the required data processing agreements,
- consulting with the Data Protection Officer (DPO) appointed by the data processor,
- helping organizations accomplish IT related tasks,
- developing policies and procedures required by the Regulation.
- if required, implementing technological solutions to ensure compliance.
Taking into account that national supervisory authorities (including the Hungarian National Authority for Data Protection and Freedom of Information) are entitled to monitor the enforcement of data privacy rights and, in case of breaches to impose a fine up to EUR 20 million or up to 4% of the annual worldwide turnover, kancellar.hu lays particular emphasis on compliance.
TRAINING
-
INFORMATION SECURITY TRAINING
Information security is not only a technological issue; the behaviour of IT users significantly affects the security level of an organization. Security awareness is best raised through training where users are shown the right behaviour as well as the consequences of typical human mistakes in an interactive training workshop.Topics:
- The philosophy of information security
- Basic IT security terms
- Legal background
- The forms of technical and nontechnical attacks
- Security-related regulations
- Incident management.
-
INFORMATION SECURITY AWARENESS PROGRAMME
Humans are the weakest link in information security. The most effective way to mitigate human-related risks is to raise employees’ security awareness in a regular and organized manner. As security awareness can have different meanings at different levels of the organization, a good security awareness programme should take characteristics of the organization and special needs of user groups into account.Our tailor-made information security awareness programme is made up of three steps:
- Making an assessment of the current situation;
- holding security awareness training for four user levels (management, users, IT staff, security staff);
- recommending measures to improve information security.
The awareness programme is a year-long series of activities with training courses, newsletters on specific topics, games and competitions to educate employees and raise their awareness. Kancellar.hu recommends that training sessions should be held at different levels as the different groups have different impact on the information security chain.Within our services we recommended special training programs for the following groups:- security awareness training for all users;
- security awareness training for the top management;
- training for IT administrators and developers;
- training for information security professionals.
SECURITY SYSTEM INTEGRATION
-
IMPLEMENTING CENTRALISED LOG ANALYSIS SYSTEMS
Managing operational risks should be an integral part of the organization’s general business risk management system. Collecting and processing system logs play an important role in managing operational risks. A Security Information and Event Management (SIEM) system enables organizations to store and analyse isolated events/logs and to ensure compliance with regulations.Our services include:
- assessing and documenting requirements for a SIEM system including:
- identifying legal, industrial and business requirements,
- assessing functional requirements for the system to be implemented;
- developing interface connections not supported by manufacturers;
- implementing systems;
- defining incident management processes;
- in addition to built-in reporting tools, developing customized reporting tools to meet the organization’s needs;
- providing training at different user levels (users, operators, administrators);
- documenting the process of implementation in detail (system design, testing plan, test reports, operating documentation, training materials).
On request, after implementation we offer our managed incident response services in accordance with the organization’s incident management policy. - assessing and documenting requirements for a SIEM system including:
-
PERIMETER SECURITY – DESIGNING AND IMPLEMENTING FIREWALLS, INTRUSION PREVENTION AND CONTENT FILTERING SYSTEMS
The primary function of a perimeter security system is to protect systems against intrusion. Based on predefined rules systems are able to permit or deny connection or perform other, special actions.Our services include the following tasks:
- System design.
After assessing the needs of the organization as well as legal and business requirements, a system design document will be created. The document contains the location of security tools within the network. The specific components will be configured in accordance with the rules described in the IT security policy. - Deployment
Once the rules for authorized traffic are implemented, functional tests are used to check that only planned connections are permitted between the zones. This will be recorded in a testing report which will be signed by the organization’s representative and then the system can go live. A detailed system documentation will be created about the new hardware and software solutions of the operating environment. - Training
On request, kancellar.hu will give training for the selected staff in managing newly implemented products. The first phase of the training will focus on describing each function of the recommended product, giving a detailed presentation of configuration options and providing an opportunity to test the product. Our experts will work together with the participants to model the future network infrastructure in kancellar.hu’s training room. In the second part of the training the participants will become familiar with installation and configuration processes.
URL, content and virus filtering technologies will be achieved in a transparent way integrated with the firewall. All network packets go through the IPS and are analysed online by the system that then blocks or allows traffic based on predefined rules.We offer the products of the following manufacturers: CheckPoint, Palo Alto, McAfee, Cisco, Symantec, and IBM. - System design.
-
SECURITY HARDENING
The objective of systems hardening is to reduce the exposure of systems to risks by blocking unused services and changing parameters. When hardening a system, we first assess the IT functions of the selected server, then we analyse the services running on the server as well as their parameters. We evaluate all services and parameters in light of their functions and services that are not needed, are removed and the system is re-configured.Our services include the following tasks:
- reviewing server(s) at the level of the operating system, performing necessary change(s), preparing, testing and configuring hardening settings/tools;
- mapping system (to show server applications, their connections with other internal and external systems);
- reviewing security settings of server applications (e.g. where and how authentication is performed in Oracle);
- assessing/analysing and documenting the operating environment, networks, connections, services and operational processes of the specific servers;
- proposing hardening solutions and, if possible, testing them in a test environment;
- implement hardening solutions, modifying and working out operational processes;
- developing customized monitoring methods and processes.
We implement hardening solutions of the specific servers and produce a hardening document.
SUPPORT AND MANAGED SECURITY SERVICES
-
OPERATING MANAGED SECURITY TOOLS
IT security tools (IDS/IPS, content filters, firewalls, virus protection systems) usually require round-the-clock monitoring. Moreover, the configuration of these systems requires special knowledge since a single configuration error can cause service interruption in the entire IT infrastructure or leave systems without adequate protection.Our experts are experienced in operating and auditing IT security tools of various manufacturers.We create a service level agreement containing the conditions for support period, response time, details of issue resolution, method and form of communication. For handling unique client needs, we categorize requests in an IMACD (Install, Move, Add, Change, Delete) system where each typical user request has a predefined score value and the fees to be paid for a given period includes a fixed amount of scores.Our services include:
- installing and configuring applications, updating new versions;
- maintaining rules, developing new rules;
- performing server operating system management tasks;
- handling system alerts;
- reporting;
- documenting administrator tasks performed in the system;
- archiving log files;
- escalating product errors and malfunctions to the manufacturers and installing the released patches.
-
OUTSOURCED CHIEF IT SECURITY OFFICER SERVICE
The tasks of an IT security officer are complex and require an interdisciplinary approach. They are required to conduct technological tests, develop and train policies and procedures, be familiar with IT systems operational duties and must communicate with system administrators, business leaders and the legal department. In our experience, such experts are very rare and extremely expensive. Yet, the majority of organizations cannot afford to employ several employees to for each competence.Our service has been designed to address this problem. Kancellar.hu will take over the responsibilities of the Chief IT Security Officer. We guarantee that each task will be performed by professionals who are experts of the given field. At the same time, we will appoint two members from our staff (a manager and his/her deputy) who will have sufficient knowledge about the daily tasks of your organization.The service starts with an intensive learning process during which we gather information about the key participants and the IT security environment. Then we will develop an annual audit plan and a security development concept plan. After the approval of the plans, we will start work in accordance with the conditions of the agreement.Our services include:
- assessing your organization’s IT security environment;
- developing annual security audit plan and security development concept plan;
- conducting planned security tests;
- if required:
- performing IT security enhancements;
- providing ad-hoc IT security services, such as:
- IT security awareness programs, training,
- representing security issues in change management,
- representing security issues in implementing new systems and in major IT development projects.
QUALITY ASSURANCE SERVICES
-
QA SERVICES FOR IMPLEMENTING SECURITY PRODUCTS
In recent years security products have become just as complicated to implement as general IT solutions. Take a firewall system for instance: its seemingly simple implementation involves several issues (licensing, scalability, supported protocols, setting up VPN) that can considerably influence the choice of manufacturer or the process of implementation (training, planning migration processes, testing).We offer you our practical knowledge acquired in security product implementation.Within our service we provide services for the entire lifecycle of security product implementation (e.g. firewall, IDM system, log management solutions etc.). The phases of the project are as follows:
- Assessment of your needs to understand all critical aspects of your security problems in order to define specific business, legal and technological requirements of the product;
- drawing up of a concept and strategy plan which contains the method and schedule of security product implementation taking into account the organization’s capabilities for change and the complexity of the task;
- active participation in the project from compiling the Request for Proposal to evaluating suppliers and assisting in concluding the agreement;
- continuous cooperation with selected suppliers in the project implementation phase, representing your company in progress meetings, strategic monitoring of the project phases (especially when the system goes live);
- monitoring of the closing phase of the project, evaluation of the project after delivery and assisting in drawing up the support agreement.
Our services include the drawing up of the following documents:- Specification of requirements
- Feasibility study
- Concept and strategy plan
- Entire bidding documents (in a tender)
- Request for Proposal
- Technical specifications
- Sample agreements
- Evaluation and presentation of proposals
- Evaluation criteria
- Reviewing project products
- Notes
- Reviewing support agreements
-
SECURITY CONSULTING FOR INDIVIDUAL SOFTWARE DEVELOPMENT
Developing new software is a complex task involving a lot of uncertain and consequently risky issues. Today no software products can be implemented without taking the security environment and security requirements into account.In our experience neither customers nor developers pay sufficient attention to security issues due to lack of experience and practice. As a result, the integration of security into the development process is a great challenge as security requirements are often in conflict with developers’ practice and business needs, especially in case of third-party software developments.We can help you identify security requirements, communicate them to developers and enforce them by monitoring the whole development process.Please note that it is advisable to define security requirements as soon as the task is formulated as in the majority of cases the requirements have a direct impact on costs and on the system to be implemented, and they usually influence the contents, the scope and the schedule of proposals (especially if third parties are involved).Our services include:
- Analysis of the system’s security environment (operation, business, and physical environment);
- Evaluation and documentation of security requirements;
- Representation of IT security aspects in tender meetings;
- evaluation of IT controls built-in into the bidder’s development methodology;
- monitoring of the development process and evaluation of deliverables from an IT security perspective;
- IT security consulting throughout the entire project;
- system security tests (ethical hacking, code analysis, testing of security functions);
- supervising of the process of going live;
- review of the system operational documents;
- review of the security clauses of the support agreement;
Within our service the following deliverables will be provided:- a description of the security problem (security environment, requirements)
- a list of functional security requirements,
- notes about the proposals,
- an evaluation of the suppliers’ development methodology from a security perspective,
- a security test plan.
Schedule of the project: depending on the implementation project, at least two months before the deadline for defining requirements. -
SOFTWARE DEVELOPMENT SECURITY CONSULTING FOR DEVELOPERS
Whether the product is individually developed software or an out-of-the-box solution, security cannot be separated from software development as security is not a product nor a feature but the result of a process. This notion led Microsoft to introduce its own software security lifecycle model (Security Development Lifecycle). In our experience, software designers nowadays do not use an organized, process-related methodology when addressing IT security issues.If your organization has its own developing team, whose developments are used in critical business processes, but their development methodologies do not include handling of security issues, this service has been designed for you.Our experts are experienced in methods applied by both the bad guys (code-breaking techniques, exploiting design deficiencies) and the good guys (ethical hacking, code analysis, threat modelling). Within our service, we offer developers to learn these skills in a hands-on learning environment.Our services include:
Depending on the development model of the organization we will assist you in creating a secure development methodology in the following areas:- security awareness training
- working out technology-specific methods of secure development,
- implementing vulnerability analysis tools
- implementing secure coding rules
- threat modelling for existing systems, integrating techniques in the development cycle,
- conducting penetration tests,
- performing security code reviews,
- introducing secure development life cycle,
- assessing maturity,
- creating and managing a development programme.
The project starts with a preliminary assessment and then we will work together with your organization to draw up a strategy plan. We will help you implement the new techniques according to the strategy plan.